Cyber Security & Architecture for Business
APPLICATIONS : SYSTEMS : INTEGRATION : MOBILE : CLOUD : INFRASTRUCTURE
Risk Assurance
Risk management practices are essential for safeguarding critical information against cyber security threats. We apply security risk-management techniques to ensure your cyber security defences are specific to the needs of your organisation.
Targeted Solutions
The costs of implementing a comprehensive information security framework such as ISO 27K or NIST 800-53 can be high. Our services will help you to identify, implement and test a tailored set of security controls that deliver the greatest value from the outset.
Cost Effective
Our aim is to deliver both high quality services and value for money. We operate a low-overheads model and as such all our cyber security services are all competitively priced.
Services
Cyber Security Architecture
Whether you are in the cloud, on-prem or a hybrid, our architecture services will ensure your technology platform can tick all the right boxes in terms of security, availability, integrity, confidentiality and privacy.
Information Security Management
If you are implementing an information security management system, we can support you throughout the entire process.
Penetration Testing
Our penetration testing service offers a pinpoint vulnerability assessment that encompasses applications, networks and infrastructure.
Threat Modelling
Our threat modelling workshops will enable you to identify the security threats to your critical information.
Recent Posts
Securing AWS S3 Websites Behind CloudFront
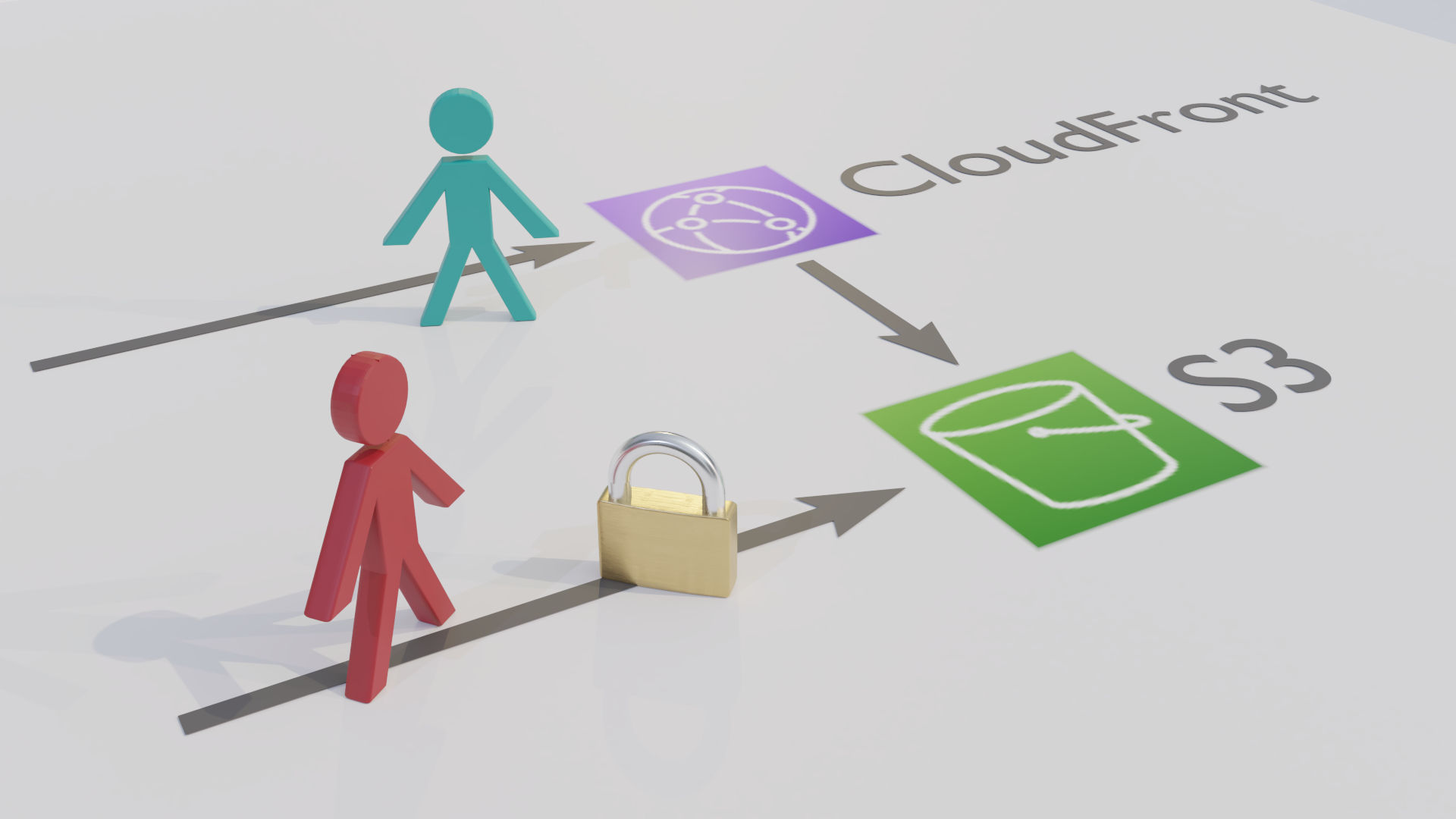
If you are hosting a site out of an AWS S3 bucket and serving up the content through Amazon’s CloudFront, you will almost certainly want your visitors to access the site through the CloudFront route rather than going directly to the Web endpoint on the S3 bucket. In this post, we’ll look at how we can easily restrict this backdoor access using an S3 policy.
Building and Leading an Effective Threat Modeling Program
I’m pleased to announce that my course, Building and Leading an Effective Threat Modeling Program, is now live on Pluralsight.
Jump Starting Information Security Management

Do you need to establish your cyber defences in a hurry? In this article we’ll look at some techniques for getting immediate benefits from the implementation of an information security management system (ISMS).
Securing HL7

If you’ve worked with IT in the healthcare industry you’ll likely be familiar with HL7. HL7 V2 is the de facto standard for systems to exchange health information messages. The standard defines the type of messages and their structure but has little to say about how the information is secured. In fact, the standard explicitly states that information security is outside of its scope.



